✅ The 7-Point Inspection — How to Tell if an Email is Fake
Below is a simple yet powerful checklist anyone can use when analyzing a suspicious message.
1. Inspect the Sender’s Email Address Carefully
Don’t trust the display name—the real sender is hidden in the email address. Watch for:
- Impersonation using generic domains
support@paypal.com@gmail.com 🚩
- Slight domain manipulations
amaz0n.co → fake
rnicrosoft.com (rn instead of m) → fake
Tip: Hover over the sender or tap for details on mobile to reveal the full email origin.
2. Watch for Unusual Tone or Language
Professional organizations use consistent formatting and clean grammar. Red flags include:
- Emotionally charged language (“account suspended”, “final warning”)
- Strange tone shifts—too formal or overly casual
- Slight grammatical errors typical of AI-generated scams
3. Hover Before You Click Any Links
Links are phishing traps 🪤. Before clicking, hover (desktop) or long press (mobile) to preview:
- Mismatched domain links
https://paypal.com → OK
https://paypa1-security.com/login → ❌ Fake
- Suspicious redirects or tracking URLs
Learn more about safe verification in our guide:
4. Treat Attachments as Dangerous by Default
Malware is often disguised as invoices or resumes:
- .exe, .js, .scr, .zip attachments → Dangerous
- Unrequested documents (e.g. “Invoice #4598”) → Be cautious
5. Beware of Generic Greetings
Fake emails often start with plain greetings:
- “Dear Customer,”
- “Dear User,”
- “To Whom It May Concern”
Real companies usually address you by name.
6. Never Share Personal Information via Email
Legitimate organizations never ask for:
- Passwords 🔑
- Bank PINs 💳
- Scans of IDs or passports 🛂
7. Check Branding Details
Even if the sender uses real logos, scammers often miss:
- Consistent branding or colors
- Proper alignment and formatting
- Updated logos or legal footer text
🔧 Technical Verification — How to Check if an Email Address Is Real
Time for definitive confirmation methods used by developers, security teams, and SaaS businesses.
✅ Method 1: Use an Email Verification API (Fast + Reliable)
Email verification APIs check if an email exists—without sending a message.
These tools:
- Validate syntax
- Confirm MX and DNS configuration
- Safely ping email servers
- Detect disposable or fake email providers
🔐 Best for: Sign-up forms, CRM cleaning, fraud prevention
✅ Try this free tool: AbstractAPI Email Verification API
It can also detect temporary emails—a common problem in fake registrations. See how it supports anti-fraud systems in: 🔗 How to Prevent Fake Signups With APIs
📬 Method 2: Double Opt-In Confirmation
A classic but effective method:
- User signs up
- They receive a confirmation link
- The account activates once the link is clicked ✅
This confirms that:
- The email address is valid
- The user owns the inbox
- Typos don’t ruin registration flows
🛡️ Method 3: Check SPF, DKIM & DMARC Authentication
Authentication records help prevent email spoofing:
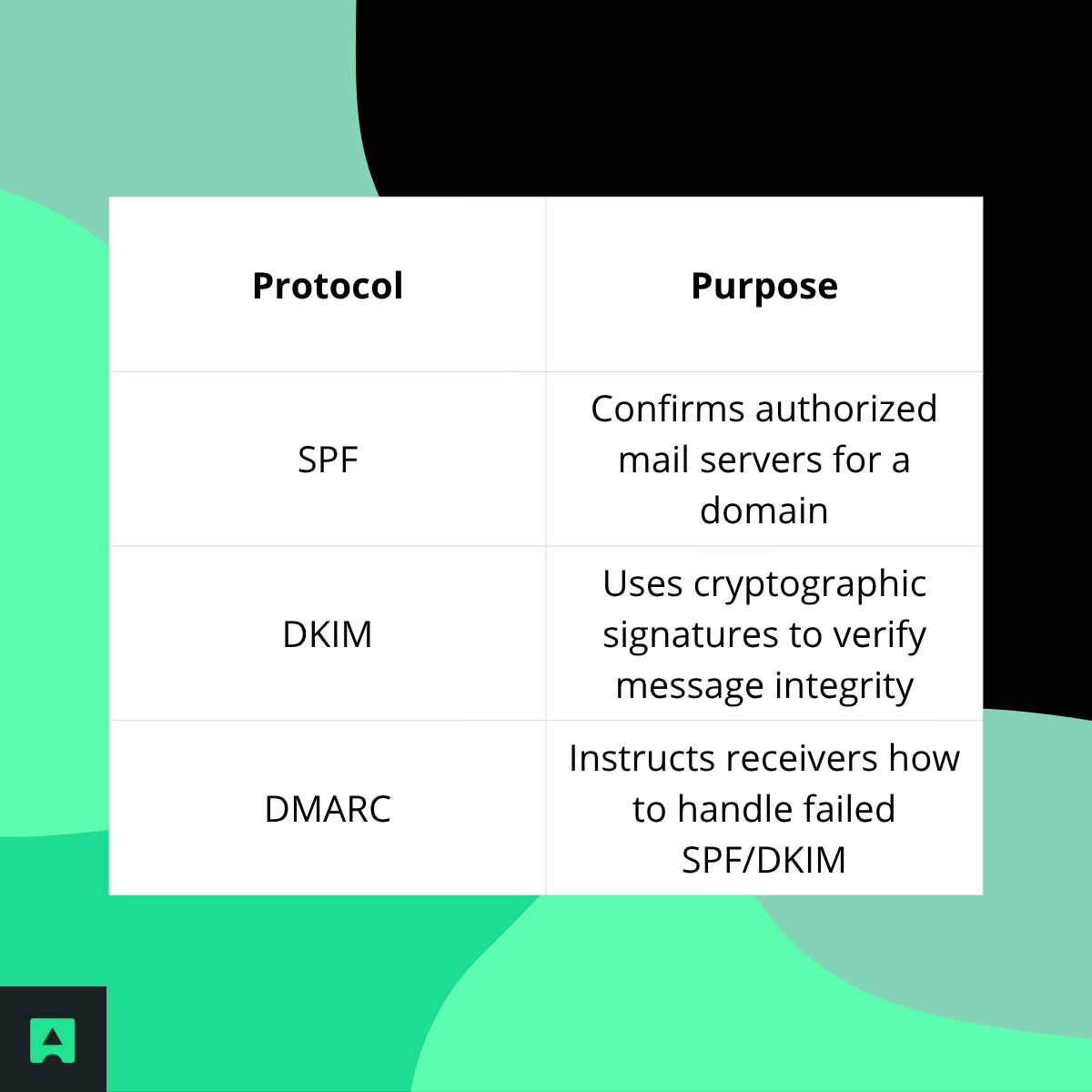
You can inspect these in the headers of a suspicious email.
🕵️ The Investigation — Trace a Fake Email and Find Its Owner
🔎 Part 1: Can You Trace a Fake Email?
Absolutely. Start with the email header. It reveals:
- The sender’s IP (sometimes hidden by Gmail/Outlook)
- The path it traveled through mail servers
- Authentication status
To view headers:
- Gmail → More → Show Original
- Outlook → File → Properties
- Apple Mail → View → All Headers
Then use an Email Header Analyzer to decode it.
Want to deepen email security? Read:
🧭 Part 2: 8 Ways to Discover Who Owns an Email
Here’s a practical investigation framework:

✅ Final Thoughts — Build Stronger Email Defenses Today
Fake emails are now nearly indistinguishable from real ones—trusting your inbox blindly is risky. But now you have a layered strategy to stay safe:
✅ Inspect manually — look for warning signs
✅ Verify technically — confirm mailbox authenticity
✅ Investigate when needed — trace suspicious senders
If you’re developing a web app, online marketplace, or subscription platform, don’t let fake emails into your system in the first place.
🔒 Protect your signup forms and user database with real-time validation:
👉 Try AbstractAPI’s Email Validation API
You may also like:




