🔑 Why API Validation Matters — The Three Pillars
API validation is more than checking field types—it’s part of a defensive architecture. Let’s break down the three strategic pillars that define why validation should be treated as a priority.
🔐 1. Security – Your First Layer of Defense
APIs are usually public-facing and accessible 24/7—making them favorite targets for attackers. Every request is a possible attack, so every piece of incoming data must be treated as untrusted until it passes verification.
Validation protects against:
- SQL Injection (SQLi)
- Cross-Site Scripting (XSS)
- Command Injection
- Path Traversal
- HTTP Parameter Pollution
- JSON bombs and malformed payloads
🚫 Example Threat: { "username": "'; DROP TABLE users; --" }
Without validation, polluted input can propagate through your application and become catastrophic. Validation acts like a shield—the earlier attacks are blocked, the safer your stack is.
👉 Want to go deeper into security best practices? Check out:
API Security Best Practices: How to Protect Your APIs
📊 2. Data Integrity – Keep Your Database Clean
Corrupted data silently destroys systems from the inside. Say you have a purchase API, and someone sends: { "productId": "123", "quantity": -5 }
If your backend processes that, you now have impossible records in your database. This kind of bad data:
- Breaks analytics and business reports 📉
- Causes refund or stock errors 🛒
- Damages trust with users and stakeholders 🔧
Validation guarantees data consistency across services—critical in microservices, event-driven systems, and distributed architectures.
⚙️ 3. Performance & Reliability – Protect Your Resources
Every invalid request that reaches your business logic or database wastes:
- CPU cycles
- Network I/O
- Memory allocations
- Database connections
By failing fast (rejecting invalid data early), you improve performance and resilience—especially under high load.
🚀 Effective validation:
- Reduces API latency
- Protects against resource exhaustion
- Mitigates DoS (Denial-of-Service) vulnerabilities
If you care about performance, you'll also like:
API Rate Limits: A Complete Guide
🧭 What is Validation in API? A Taxonomy You Can Use Today
Validation can be organized in a multi-layered model, covering input, business logic, and responses. Let’s break it down.
🛡️ Input Validation – Guard the Gateway 🔑
Input validation filters all incoming data before it touches your logic.
✅ Layer 1: Syntactic Validation – Check Shape & Format

🧠 Layer 2: Semantic Validation – Enforce Meaning
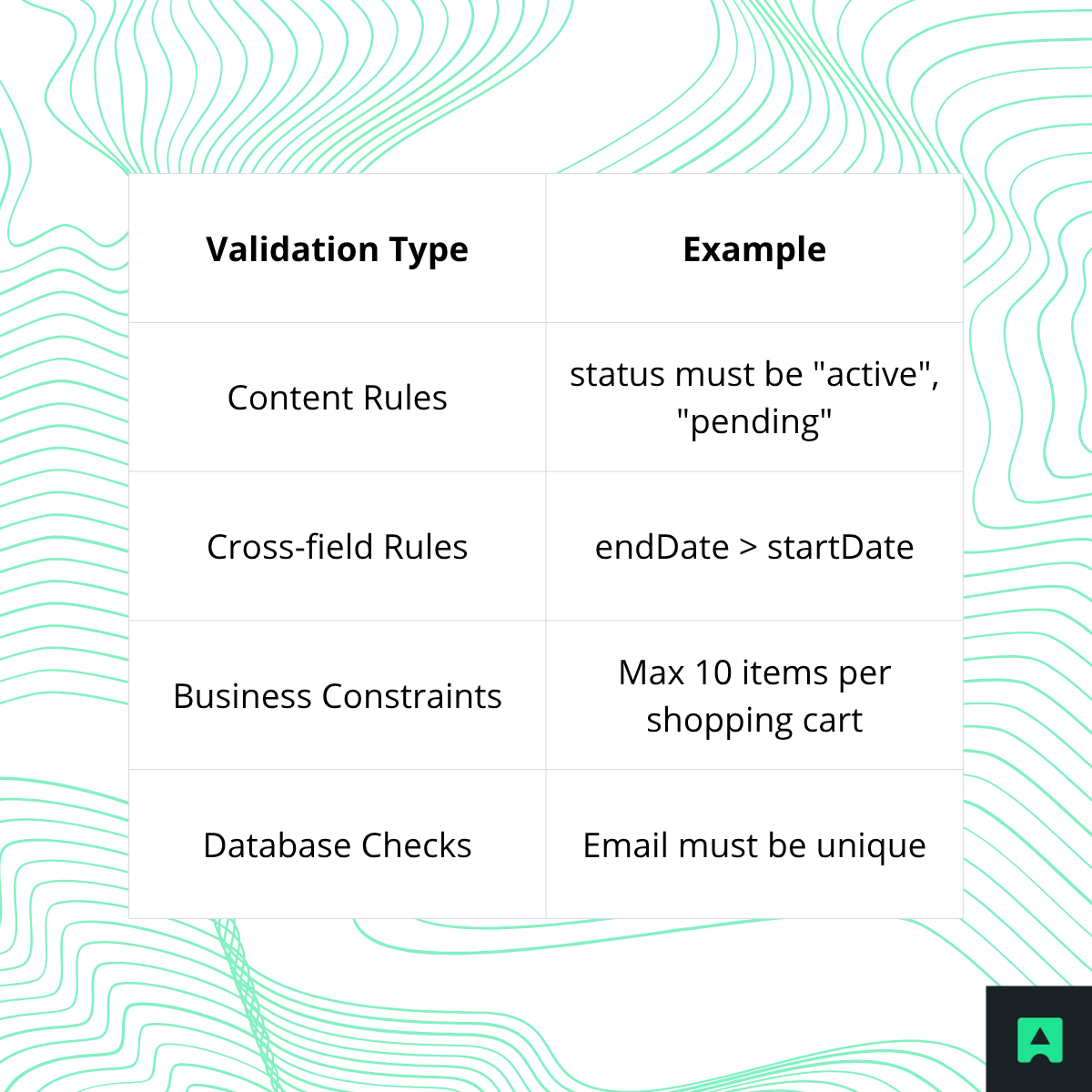
🔒 Output Validation – Don’t Leak Sensitive Data
Many developers overlook response validation, but it's a crucial security layer.
✅ Output validation ensures:
- You never expose private/internal fields (passwordHash, internalId)
- Sensitive logs or stack traces don’t leak
- Error messages don’t reveal system behavior
💡 Related reading:
REST API Response Standards: Best Practices
🛠️ How to Implement API Validation (the Right Way)
Validation isn't a single step; it's a multi-phase defense pattern.
✅ Where to Validate
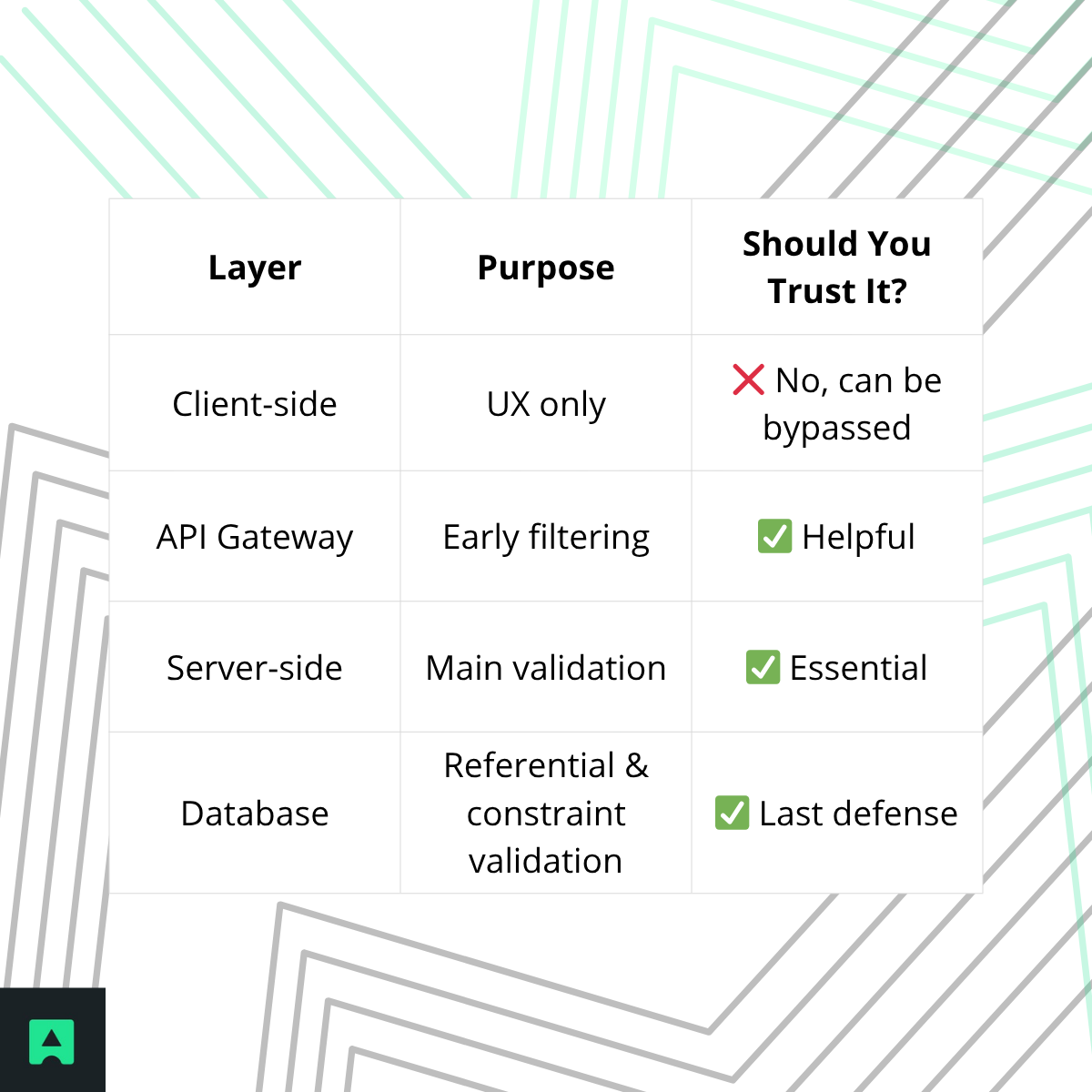
📦 Code-Level Validation — Practical Examples
JavaScript with Zod
import { z } from "zod";
const userSchema = z.object({
email: z.string().email(),
age: z.number().int().min(18),
});
const result = userSchema.safeParse({
email: "not-an-email",
age: 22
});
Python with Pydantic
from pydantic import BaseModel, EmailStr, conint
class Signup(BaseModel):
email: EmailStr
age: conint(ge=18)
Signup(email="test@example.com", age=17) # Raises validation error
🚨 API Error Handling Done Right
Use clear, structured error messages. Good APIs fail gracefully.
❌ Poor Error: { "error": "Invalid input" }
✅ Professional API Error:
{
"error": "Validation failed",
"issues": [
{ "field": "email", "message": "Invalid email format" },
{ "field": "age", "message": "Must be at least 18" }
]
}
Use HTTP codes correctly:
- 400 Bad Request → syntax error in request
- 422 Unprocessable Entity → wrong but well-formed data
- 409 Conflict → violates business constraint
🔧 Best Practices for API Validation
✅ Validate everything at boundaries
✅ Reject unknown fields (enforce schema contracts)
✅ Never trust client-side validation alone
✅ Keep validation logic close to data models
✅ Log validation failures for debugging & security
✅ Sanitize, don't just validate
✅ Use validation libraries—not custom regex everywhere 🚫
💡 Real-World Validation Needs Real-World Data
Basic regex validation isn’t enough for real systems. You need to check if data actually exists and works.
Example:
- "john@mail.com" → valid email format ✅
- But does it accept mail? Or is it disposable mail? ❌
That’s when powerful validation APIs come in 👇
✅ Validate real user emails →
👉 AbstractAPI Email Validation
✅ Check if phone numbers are real & callable →
✅ Detect risky IPs & suspicious requests →
These APIs integrate easily and offload complex validation rules so you can focus on business logic.
Final Thoughts
API validation is more than checking inputs—it’s a security strategy, a data protection mechanism, and a performance optimization tool.
Remember the 3 pillars:
✅ Security
✅ Data Integrity
✅ Performance
Treat validation as a must-have architectural layer, not an afterthought.



