Can you truly hide your IP address?
The short answer: not exactly. There’s no way to make your IP completely vanish—it’s required for your device to communicate online. However, you can disguise it so that websites and services see a different IP than your own.
Think of it like sending a package 📦. Instead of putting your home address on the return label, you use the address of a trusted forwarding center. The package still has a return address, but it doesn’t directly reveal where you live.
This “masking” is how tools like VPNs, proxies, and Tor work—they let you borrow another IP so your real one remains hidden from prying eyes.
Is hiding an IP address illegal?
Here’s the good news: hiding your IP address is not illegal ✅. Millions of people worldwide use methods like VPNs every day for totally valid reasons, such as protecting themselves on public Wi-Fi or accessing services while traveling.
That said, the legality comes down to what you do while your IP is hidden.
- Using a VPN to secure your data at an airport lounge = perfectly legal.
- Using that same VPN to engage in cybercrime = still very much illegal.
So, the technology itself is lawful, but like any tool, it can be misused. Responsible use is the key.
The Main Methods: How to Mask Your IP Address
There are three main tools people use to disguise their IP addresses. Each comes with different levels of security, speed, and complexity. Let’s explore them in detail:
1. VPN (Virtual Private Network) 🔒
A VPN is the most popular and versatile option for masking your IP. When you connect to a VPN, all your internet traffic is encrypted and routed through a secure server operated by the VPN provider.
How it works: Imagine you’re writing messages in a secret code that only you and your friend know. Even if someone intercepts your letters, they can’t read them. Similarly, a VPN encrypts your internet activity so hackers, your ISP, or snooping governments can’t easily see what you’re doing.
Best use cases:
- Securing data on public Wi-Fi (airports, cafés, hotels).
- Streaming content from another country (e.g., watching a U.S. streaming catalog while abroad).
- Keeping your browsing activity private from ISPs.
Advantages:
✅ Strong encryption keeps your personal information safe.
✅ Easy-to-use apps on all devices (iOS, Android, Windows, Mac).
✅ Wide choice of server locations worldwide.
Drawbacks:
❌ Quality VPNs often require a paid subscription.
❌ Can sometimes slow your connection slightly, depending on server distance.
Quick example: Connecting to a VPN server in London while you’re in New York will make websites think you’re browsing from the UK 🇬🇧.
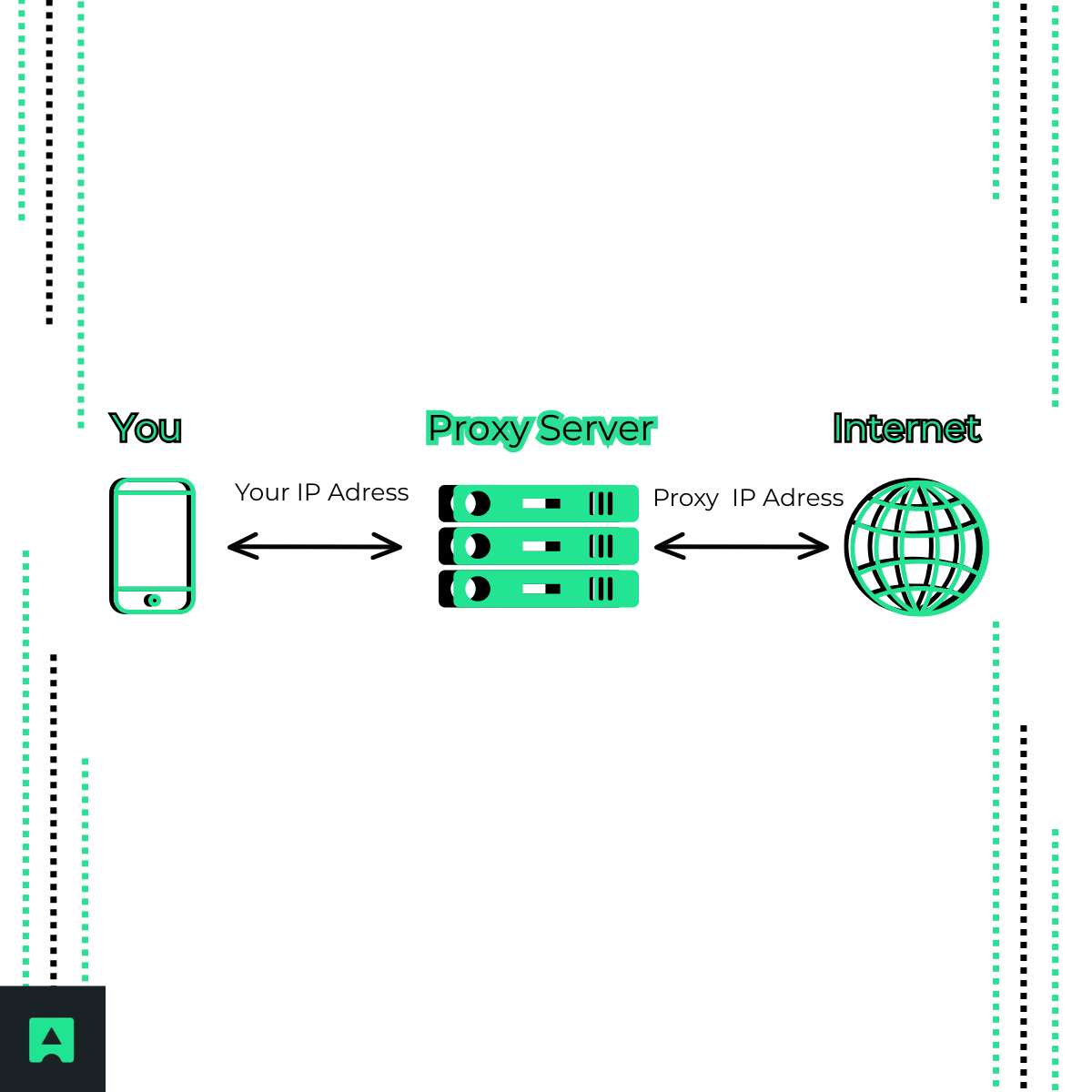
2. Proxy Server 🌐
A proxy server is like a middleman between your device and the internet. Instead of your requests going directly to a website, they go through the proxy first. The website then only sees the proxy’s IP address.
How it works: Think of a proxy like a receptionist. You hand them a note, they deliver it to the intended person, and then bring the reply back to you. The recipient never interacts with you directly—only with the receptionist.
Best use cases:
- Quickly bypassing basic geo-restrictions on websites.
- Accessing content where privacy isn’t your top concern.
- Lightweight tasks like scraping publicly available data (when allowed).
Advantages:
✅ Often free or inexpensive.
✅ Simple to configure in browsers.
✅ Can switch IPs quickly for testing different locations.
Drawbacks:
❌ Most proxies don’t encrypt traffic, so data can still be intercepted.
❌ Some proxy providers may log your activity.
❌ Not ideal for sensitive tasks like online banking.
Quick example: If a website blocks traffic from your country, a proxy based in another region can let you bypass the restriction temporarily.
3. Tor Browser 🕵️♂️
Tor (The Onion Router) is designed for maximum anonymity. Instead of routing your traffic through one server, it bounces it through multiple servers (called “nodes”), each adding a layer of encryption.
How it works: Picture an onion 🧅 with multiple layers. Each server in the Tor network peels off one layer of encryption, but no single server knows both where the request came from and where it’s going. This makes tracking extremely difficult.
Best use cases:
- Communicating in high-censorship environments.
- Protecting identity for journalists, activists, or whistleblowers.
- Browsing anonymously without leaving a clear digital footprint.
Advantages:
✅ Provides very high levels of anonymity.
✅ Completely free to use.
✅ Decentralized—no single company controls the network.
Drawbacks:
❌ Can be very slow compared to VPNs and proxies (due to multiple hops).
❌ Some websites block traffic from known Tor exit nodes.
❌ Not ideal for streaming or large downloads.
Quick example: An activist in a country with strict censorship laws could use Tor to access news websites that are otherwise blocked locally.
👉 As you can see, no single method is “best” for everyone. If you value speed and security, go with a VPN. If you just need a quick IP switch, a proxy works. If anonymity is your top priority, choose Tor.

How do I mask my IP address without VPN?
If you don’t want to use a VPN—or maybe you can’t install one on your device—there are still other ways to disguise your IP. The two most common alternatives are:
- Proxy servers → These work as a middle layer between your device and the websites you visit. They’re useful if you simply need to change your visible location to access a site that’s blocked in your region. However, most proxies don’t encrypt your traffic, so your browsing activity could still be monitored. Think of them as a “quick fix” rather than a robust privacy tool.
- The Tor Browser → Tor takes a very different approach by routing your traffic through multiple volunteer-operated servers around the globe. Each relay strips off a layer of encryption, making it extremely difficult to trace the activity back to you. This makes Tor excellent for anonymity, but the extra hops slow down your connection significantly. It’s better suited for private communication or browsing censored content, not streaming or heavy downloads.
👉 In short: if you just need a temporary way to change your IP address, a proxy will do the job. But if your goal is to remain as anonymous as possible, Tor is the stronger choice—though you’ll sacrifice speed in exchange for privacy.
How do I hide my IP address on my iPhone? 📱
Hiding your IP on a smartphone is easier than most people think. The most reliable method is to use a VPN app, which takes only a few minutes to set up.
Steps on iPhone or Android:
- Pick a trusted VPN provider and download its app from the App Store or Google Play.
- Create an account or log in.
- Open the app, select a server in your desired location, and connect.
From that moment, all your traffic is routed through the VPN’s server, and your real IP address is masked.
Other options: If you don’t want to use a VPN, you can try a proxy service or even browse via the Tor Browser app (available for both iOS and Android). These aren’t as straightforward, but they can still hide your IP.
For computers (Windows/Mac): The process is almost identical—download the client, sign in, and connect. Within seconds, websites will see the server’s IP instead of yours.
👉 Whether on mobile or desktop, using a VPN app is the most user-friendly way to change your IP, even if you’re not tech-savvy.
The Business Perspective: Why Companies Detect Your IP
While individuals often hide their IP addresses for privacy or convenience, companies view IP data as an essential part of online security. Every IP request carries information that helps businesses determine who is accessing their systems and whether that activity is trustworthy.
Why it matters for businesses:
- Fraud prevention: Identifying suspicious IPs (such as those linked to known VPNs, proxies, or data centers) helps stop fraudulent transactions.
- Bot detection: Malicious bots often cycle through IPs to appear legitimate, so companies monitor patterns to block them.
- Content control: Media platforms rely on IP detection to enforce licensing agreements and restrict access to certain regions.
This is where AbstractAPI’s IP Geolocation API plays a vital role. By analyzing IP data in real time, businesses can identify whether an IP is genuine or masked, helping them strike a balance between user privacy and platform security.
Conclusion
Learning how to hide your IP address is a practical step toward reclaiming control over your digital footprint. The best method depends on your priorities:
- VPNs offer the most balanced mix of security, privacy, and usability.
- Proxies are quick and simple but weaker on protection.
- Tor delivers maximum anonymity at the cost of speed.
No matter which option you choose, understanding how these tools work empowers you to make smarter decisions online 🌍.
👉 Want to see what your own IP address is revealing right now? Try the AbstractAPI IP Geolocation API
to check the kind of data websites already collect about you—and discover the real power of IP intelligence.



